2D1455 - Laboratory Exercise 1.
The Security Controller Requirements.
This series of exercises is designed to take you through the process of
object-oriented requirements analysis.
leading to a set of live sequence charts (LSCs). It will give you the chance to put into practise the analysis and modelling ideas you have learned on the course.
1. Getting Started
You will be developing your design solutions to this exercise as a hyper-linked set of web pages,
such as would be suitable to store on a companies intranet, allowing you to share your solution
with business colleagues.
To prepare for this lab exercise begin by carrying out the following task
1. Requirements Analysis
<a href= "informal_req.html">Exercise 1.1:</a> Informal
Requirements.
<a href= "data_dictionary.html">Exercise 1.2:</a>
Data Dictionary.
<a href= "use_cases.html">Exercise 1.3:</a> Use
Cases.
<a href= "req_object_model.html">Exercise 1.4:</a>
Requirements Object Model.
1. Requirements Analysis Phase
1.2. Introduction to Exercise 1
1.3. The Informal End User Requirements
1.4. Marking up the Informal End-User Requirements
1.5. Creating the Data Dictionary
1.6. Creating the Use Case Model
1.7. Creating the Requirements Object Model
In lab exercise 1 you will learn how to:
1.2. Introduction to Exercise 1
In Exercise 1 you will carry out the requirements analysis phase of an O-O design. The aim of the requirements analysis phase is to:
We will guide you through the initial steps of each exercise part. Your task
will be to continue and
complete the missing information.
Therefore you should have a clear pattern of work to follow at each stage.
1.3. The Informal End User Requirements
Your end user has asked you to produce a requirements analysis for a
computerised security control system.
The purpose of this system is to control the access to, and hence security
of, a given set of offices.
(You do not yet know the actual number or organisation of the offices. This
may or may not be revealed to you as an outside party!)
An entrance to an office can have have four different security levels:
The security levels of an office entrance can be altered during the day.
Each employee working in the office has a card with a personal code consisting of four digits.
To open a door with security level three, the employee enters his/her card into a card reader
and types the personal code on a keypad. The time between consecutive keystrokes when typing the code
is not allowed to exceed three seconds. To enter through a door with security level two, the employee just
enters the card into a card reader.
Each entrance leading into the office consists of a door with an electronic lock, and also a card reader,
a keypad and a display on the outside, an alarm and an exit button (to open the door
immediately, and for
emergency exits!) on the inside. The employee needs a card and a code to enter
the office. To exit,
the employee just presses the exit button and the door is unlocked for ten seconds.
If the door
remains open for more than ten seconds then the entrance alarm sounds. If it is intended
that the door
remain open for more than ten seconds, then its security level must be level
1, i.e. always unlocked.
All entrances communicate directly with a central controller. This system carries out validation of
the correctness of cards and codes. The controller makes use of a database
consisting of all
card numbers in use, and their corresponding personal codes. At level 3, a presented
card is
valid if the presented code matches its database record, otherwise a card is
valid if its number is
in use. If a presented card is valid, then the door at which the card is presented
is opened for
ten seconds and the employee may enter. In the case of an invalid, or unregistered
card, access
to the office is not allowed. In the case of an incorrect code, the employee
presenting the card is
informed of this and must try again by reinserting the card into the card reader
and retyping the
personal code. If the code is incorrectly typed in 4 times in succession then the card number is
invalidated by the
central controller, and the card holder must contact the system manager to gain access.
The security control system must read its data, consisting of card numbers
with their corresponding
personal codes, from a database. The database is managed with a separate management
system
that is not being developed within this particular project. The system administrator
is authorised
to validate card numbers, register new employees, cards and codes, to change a code if an employee
wishes so, to
delete employees from the database and to change the security level of an entrance.
The system
operator is also responsible for initialising the security control system, for example after a hardware repair. All
the actions described
above are done using the management system.
The system must be able to recover from computer and communication failures.
If a communication between an entrance and the central controller is lost, the door
should be locked from the outside, not permitting anyone to enter without a card and a code (i.e. the security level
is set to three). However, it is possible to open the door using the exit button.
The system must be extensible to include new functions and must be easily maintainable.
1.4. Marking up the Informal End-User Requirements
To begin the requirements analysis you will markup the informal end-user requirements text
of Section 1.3. You should perform the following steps.
Here is how your document might look after marking up the requirements concepts.
(Note: the text below
is not a complete markup as it stands.)
Informal User Requirements
An <a href= "data_dictionary.html#entrance">entrance</a> to an office can have have four different security levels:
The security levels of an office entrance can be altered during the day. ....
1.5. Creating the Data Dictionary
Now it is time to create a data dictionary. This is a text document that serves as a reference document for all technical requirements concepts. It provides a common and agreed vocabulary between the end users and the requirements analysists. Data dictionaries often contain a lot of domain specific terminology and notation, e.g. specific to the: banking sector, the aerospace sector, the insurance sector, etc. It is important that non-expert programmers understand the necessary domain knowledge sufficiently well on a project.
It is important to:
All the important nouns, relations and verbs that you found in Section 1.4 should be included in the data dictionary.
Here is how you entries might look: try to reproduce the entries below without
simply copying them.
Data Dictionary
1. Nouns/Objects
<a name="card"></a> Card - each employee working in the office gets a card and a corresponding personal code. By means of this card and code, the employee can get access to the office.
<a name="security_control_system"></a> Security control system - a system to control the access rights to an office so that no unauthorised persons can enter without permission.
2. Verb Phrases
<a name="change_code"></a> Change code - an operation done by the system operator to change the code of a card.
3. Relational Phrases
<a name="card_with_code"></a> Card with code - each employee in the office has a card with a personal code.
1.6. Creating the Use Case Model
The aim of the use case model is to capture the requirements and present them from the users point of view, thus making it easier for the end user to validate the correctness of the requirements analysis. The validation activity has been discussed in detail in the course.
The use case model consists of:
The use case model is an important source of information when developing the requirements object model.
A use case is a sequence of actions showing a possible usage of a system. Use cases developed during the requirements analysis phase mainly concern the interaction between the system and its users. No message exchange within the system should be mentioned, since we are taking a "black-box" view of the system, and developing a top-down design.
Users of a system may be people with different job descriptions or roles, or names (for one specific customer), they may also be other systems, or objects outside the scope of the design project that must interact with the system. A user is not necessarily a person.
An actor is a user taking part in a use case. An actor is not necessarily an individual user, but is more commonly a role that a user can play when interacting with the system. Notice that one and the same person may play different roles. For example, if you have a PC at home, then you are probably both the end user and the system administrator, depending on how you log in.
There are three different ways to describe a use case:
Describing a use case using text makes it easier to model exceptions and alternative paths of action sequences. Describing a use case using an LSC will make the use case more formal and easier for validation of the requirement and verification of the subsequent design and implementation. (If you are still unfamiliar with the words "validation" and "verification", try looking them up in a good book on software engineering, or on the web.
We will develop both text and graphical descriptions of use cases, to explore and compare the two.
Here is a part of how your document should look when finished:
Use Case Document
1. Actor List.
Employee: someone who needs to enter and exit the office. To enter the office, an employee must have a registered card, and (depending on the current security level) a corresponding personal code. To exit, the employee must press an exit button to unlock the door.
Central Controller: the central controller starts and maintains the security control system. All changes to the database are handled by the central controller. The central controller is operated by a system operator.
2. Use Case Summary.
Normal Cases:
Level2 Entry Describes the interaction between an employee and the security control system when an employee wants to enter the office through a door with security level two.
Level3 Entry Describes the interaction between an employee and the security control system when an employee wants to enter the office through a door with security level three.
Exceptional Cases:
Invalid Card or Code: ...
3. Text Use Cases.
Name:
Actors: Employee, Central Controller,
Door, Card Reader, Display,
Keypad
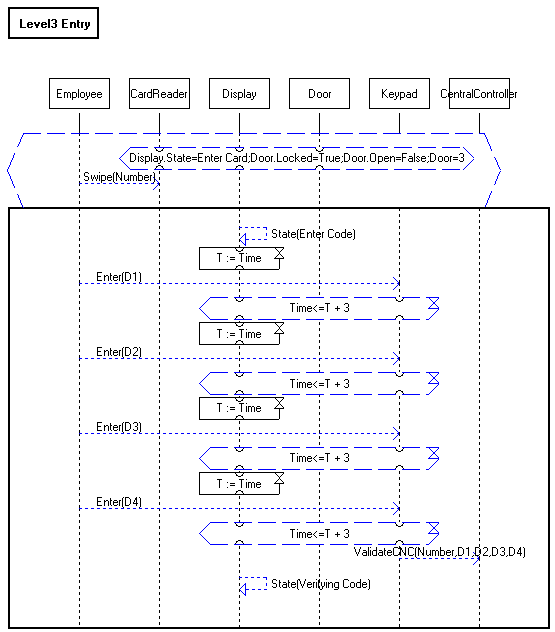
Precondition The security level of the door is three.
The door is closed and locked. The door display displays the
message "Enter Card".
Postcondition The security level of the door is three. The door is closed and locked.
The door display displays the message "Verifying Code". The central controller is verifying the code.
Description The employee swipes a card into the card reader which reads its number. The display
displays the message "Enter Code". The employee enters a code consisting
of four digits using the keypad. Each digit is entered within 3 seconds.
The card number and the four digits are sent to the central controller for validation.
Exceptions
4. LSC Use Cases.
Here is an LSC for the use case "Level3 Entry". It does not include the exception case, which would have to be drawn separately.

4. Automatically Generated Natural Language Translation.
Whenever:
If Display.State=Enter Card and Door.Locked=True and Door.Open=False and Door.SecVal=3
then continue, otherwise ignore this scenario.
the Employee sends Swipe(Number) to the CardReader
Then:
the Display its State to Enter Code,
T is assigned the current time,
the Employee sends Enter(D1) to the Keypad.
If current time<=T + 3
then continue, otherwise exit the scenario.
T is assigned the current time,
the Employee sends Enter(D2) to the Keypad.
If current time<=T + 3
then continue, otherwise exit the scenario.
T is assigned the current time,
the Employee sends Enter(D3) to the Keypad.
If current time<=T + 3
then continue, otherwise exit the scenario.
T is assigned the current time,
the Employee sends Enter(D4) to the Keypad.
If current time<=T + 3
then continue, otherwise exit the scenario.
the Keypad sends ValidateCNC(Number,D1,D2,D3,D4) to the CentralController,
the Display its State to Verifying Code.
1.7. Creating the Requirements Object Model
The requirements object model is meant to capture:
which are important for the application that is being built. Relations between objects will
be expressed through associations, aggregations and inheritance. In this final part of the exercise you need simply
display the internal object model for the security control system which the Play-Engine automatically creates.
This will help both the examiner and you understand the static structure of your requirements model.